Firewall Rules Report
The Cloudamize Firewall Rules Report helps you understand and manage network dependencies in your environment. It shows all inbound and outbound communication rules observed during the monitoring period between servers, applications, or services.
This report helps you build accurate security policies and firewall rules for your cloud migration, ensuring that all necessary connections are maintained after the move.
The Cloudamize Agent and Agentless Data Collector gather data on all application connections, including source and destination IP addresses, ports, and protocols. This information is then used to generate a detailed report that outlines the communication patterns within your infrastructure. The agent does not directly query firewalls, but rather builds a picture of required firewall ports based on detected network traffic.
Key Components of the Firewall Rules Report:
1. Source and Destination
Source: The IP address or hostname initiating the communication.
Destination: The IP address or hostname receiving the traffic.
Can also reflect machine groups or application tiers (e.g., App → DB).
2. Port
The destination port used for communication.
Helps identify the service (e.g., port 80 → HTTP, 443 → HTTPS, 1433 → SQL Server).
3. Protocol
TCP, UDP, or others.
Defines how the data is transmitted.
4. Direction
Inbound: Traffic going to the machine
Outbound: Traffic going from the machine
Steps to navigate to the Firewall Rules Report:
Log in to the console https://console.cloudamize.com/#/
Navigate to the Plan page of your completed assessment.
Click on the Reports Section as shown in the screenshot below under the Plan section.
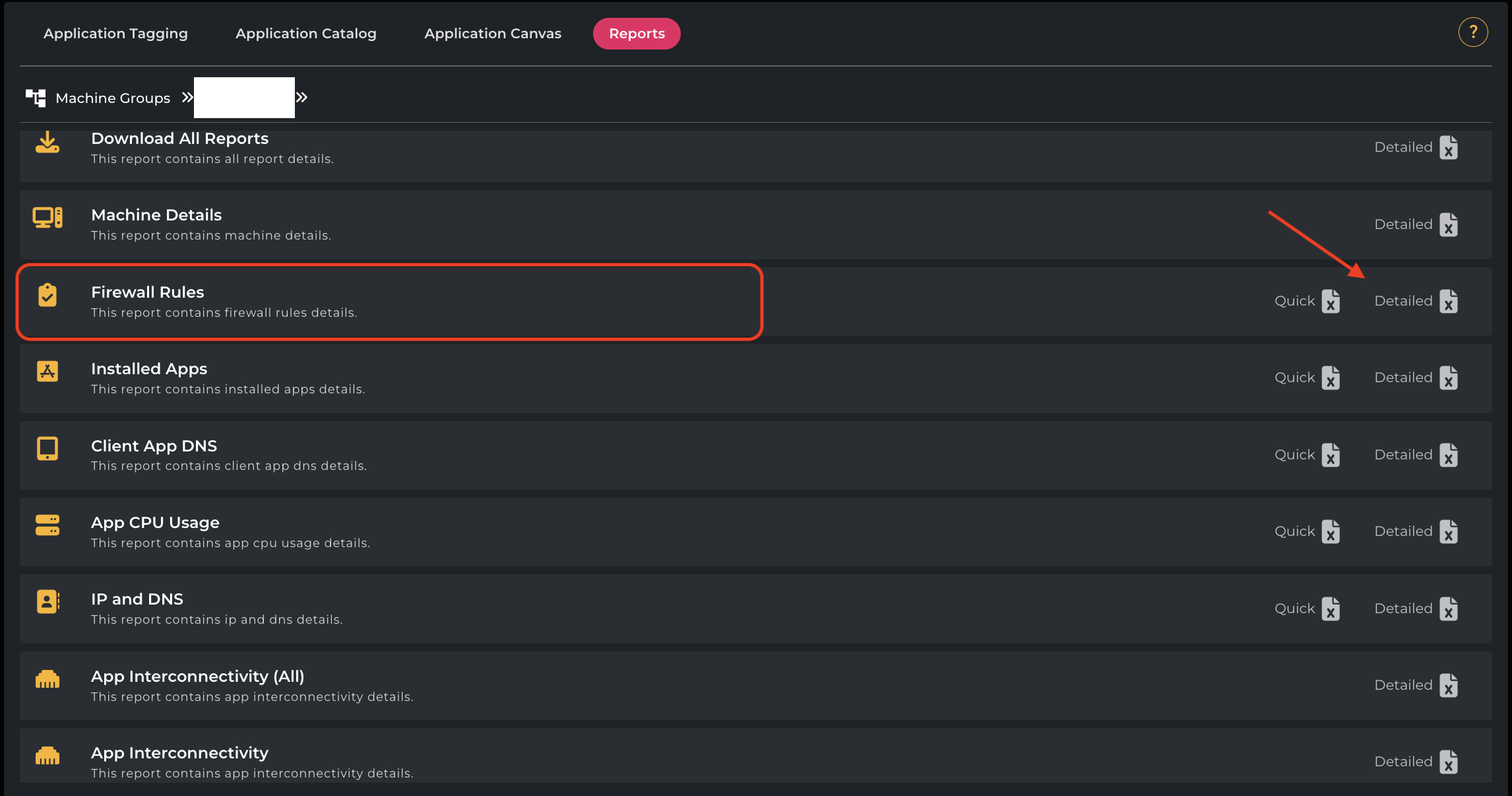
Click on Firewall Rules → Detailed to download the report.
Sheet Name | Column Name | Description |
|---|---|---|
Inbound Firewall Rules | Server Process Name | Name of the server-side process handling incoming connections. |
Server Port | Port number on the server receiving traffic. | |
Client IP Address | IP address (CIDR format) of the client making the request. | |
Group Name | Logical group or network segment to which the server belongs. | |
Asset Name | Name of the asset (application, service, or system) being accessed. | |
Instance Name | Specific instance or node hosting the asset. | |
Inbound Firewall Rule (Masked16) | Server Process Name | Same as above, but client IPs are masked to /16 subnets for privacy/security. |
Server Port | Port number on the server receiving traffic. | |
Client IP Address | Masked /16 subnet of the client IP. | |
Group Name | Logical group or network segment to which the server belongs. | |
Asset Name | Name of the asset (application, service, or system) being accessed. | |
Instance Name | Specific instance or node hosting the asset. | |
Inbound Firewall Rule (Masked24) | Server Process Name | Same as above, but client IPs are masked to /24 subnets. |
Server Port | Port number on the server receiving traffic. | |
Client IP Address | Masked /24 subnet of the client IP. | |
Group Name | Logical group or network segment to which the server belongs. | |
Asset Name | Name of the asset (application, service, or system) being accessed. | |
Instance Name | Specific instance or node hosting the asset. | |
Outbound Firewall Rules | Client Process Name | Name of the client-side process initiating outgoing connections. |
Server Port | Port number on the destination server. | |
Server IP Address | IP address (CIDR format) of the destination server. | |
Group Name | Logical group or network segment from which the connection originates. | |
Asset Name | Name of the originating asset. | |
Instance Name | Specific instance or node initiating the connection. | |
UDP Firewall Rules | Process Name | Name of the process communicating over UDP. |
Server Port | UDP port(s) used; can be individual ports or ranges. | |
IP Address | Destination or source IP involved in UDP communication. | |
Group Name | Logical group or network segment to which the server belongs. | |
Asset Name | Name of the asset (application, service, or system) being accessed. | |
Instance Name | Specific instance or node hosting the asset. |
Example Report:
