Access Network Discovery Data
Viewing the Results: Network Discovery Inventory Settings Tab
The Network Discovery Inventory Settings Tab is available under the Discovery Option. To access this tab, select the “Discover” option from the Cloudamize Landing Page.
Once the tool has completed its run and uploaded the data to the Cloudamize portal, you can view the results on the Network Discovery tab in the Inventory Settings page of the portal.
Network Discovery Tab, Prior to Data Upload
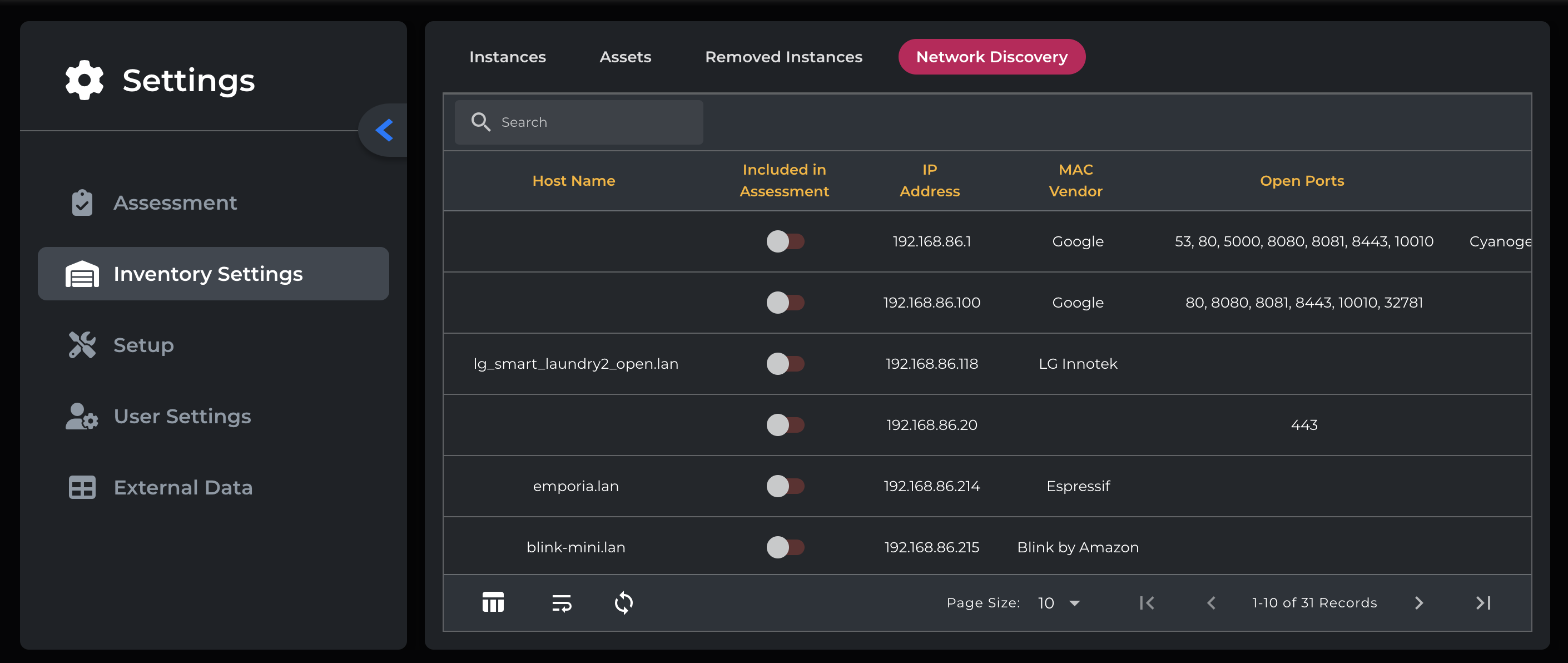
Network Discovery Tab, After Data Upload
On this tab, you can view all discovered network devices and any related details that have been discovered, labeled by column. The results are searchable using the search box in the top left.
The network discovery agent will collect the following
Hostname
Host(IP address)
MAC Vendor
Open Ports
OS Name
OS Confidence
The “Included in Assessment” column identifies any servers that are connected to the portal by a Cloudamize data collector - Agent, Agentless, Hypervisor, or vCenter connections are all valid connections. Using this, you can identify servers that aren’t currently included in the assessment and quickly add them if desired, for example, by adding their IP address to an existing Agentless Data Collector.
Support
The Network Scanner wrapper is provided as-is. Cloudamize can offer assistance in configuring the command line for the tool, but cannot offer support for the nmap tool itself.
If you have any queries, please contact the helpdesk.
